IBM QRadar Security Intelligence
Smarter threat detection for smarter threats
IBM QRadar SIEM
Rapidly detect advanced security threats in your network with real-time analytics
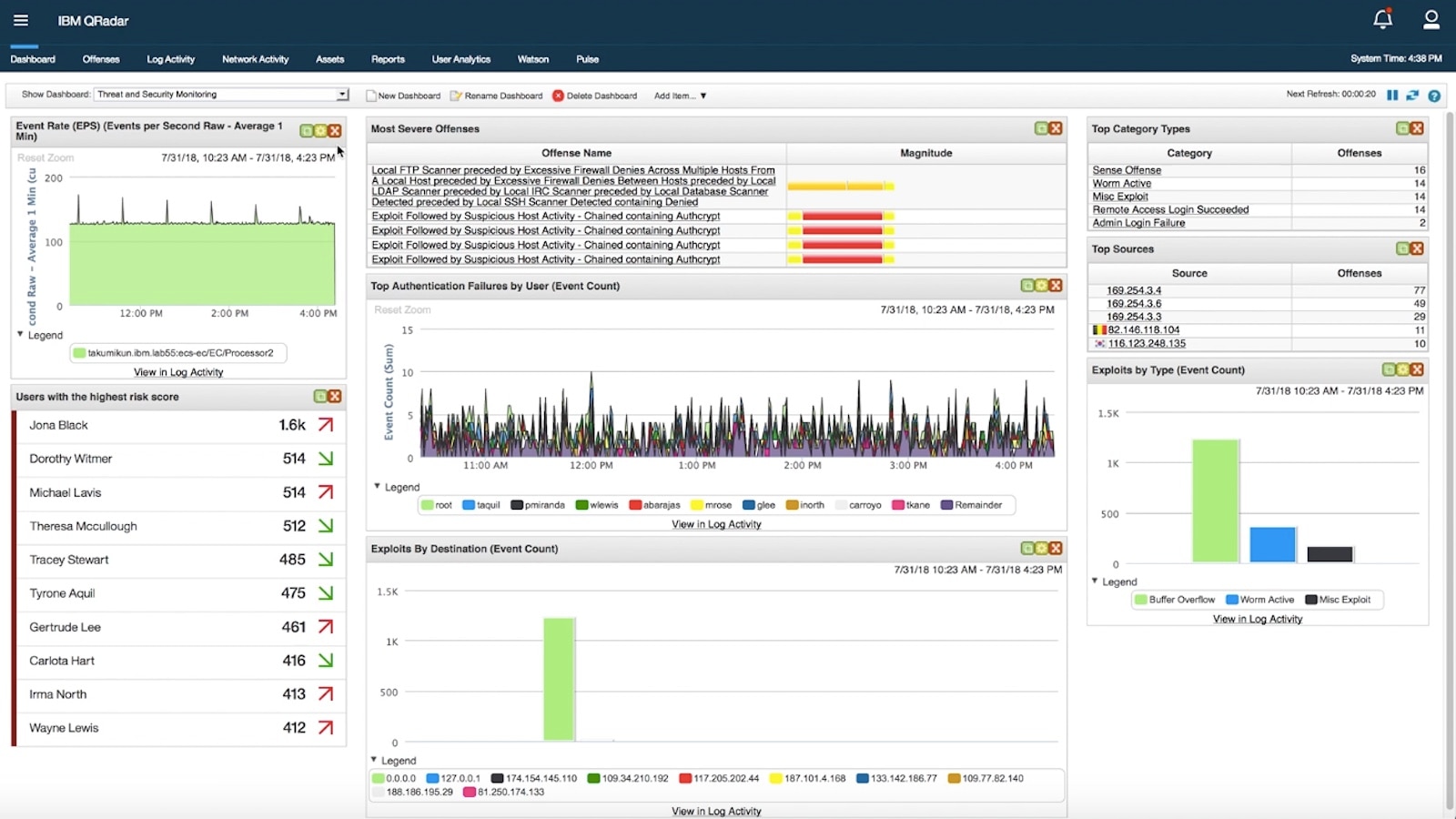
IBM® QRadar® Security Information and Event Management (SIEM) helps security teams accurately detect and prioritize threats across the enterprise, and it provides intelligent insights that enable teams to respond quickly to reduce the impact of incidents. By consolidating log events and network flow data from thousands of devices, endpoints and applications distributed throughout your network, QRadar correlates all this different information and aggregates related events into single alerts to accelerates incident analysis and remediation. QRadar SIEM is available on premises and in a cloud environment.
Comprehensive Visibility
Gain centralized insight into logs, flow and events across on-premises, SaaS and IaaS environments.
Eliminate Manual Tasks
Centrally see all events related to a particular threat in one place to eliminate manual tracking processes and enable analysts to focus on investigation and response.
Real-Time Threat Detection
Leverage out-of-the-box analytics that automatically analyze logs and network flows to detect threats and generate prioritized alerts as attacks progress through the kill chain.
Easily Manage Compliance
Comply with internal organizational policies and external regulations by leveraging pre-built reports and templates.
Key Features
- Ingest vast amounts of data from on-prem and cloud sources
- Applies built-in analytics to accurately detect threats
- Correlate related activities to prioritize incidents
- Automatically parses and normalizes logs
- Threat intelligence and support for STIX/TAXII
- Integrates out-of-the-box with 450 solutions
- Flexible architecture can be deployed on-prem or on cloud
- Highly scalable, self-tuning and self-managing database
IBM QRadar Advisor with Watson
Apply artificial intelligence to accelerate incident analysis and rapidly respond to threats.
What can Artificial Intelligence do for Security Analysis?
Security analysts feel the pressures of data overload and are often unable to manage the enormous volume of incident alerts day-to-day. This leaves businesses vulnerable to unaddressed security threats. Enter QRadar Advisor with Watson. It applies artificial intelligence to automatically investigate indicators of compromise, utilizes cognitive reasoning to provide critical insights, and ultimately accelerates the response cycle. See how IBM QRadar Advisor with Watson can augment a security analyst to gain a head start in assessing incidents and reduce the risk of missing threats.
Accelerated Analysis
Automatically investigate an incident or anomaly to identify the likely threat. Quickly gather insights from millions of external sources and local data mining.
Intelligent Investigation
Apply cognitive reasoning to build relationships among discovered threat entities and get visibility into higher priority risks, critical systems impacted, insider threats, and more.
Faster Response
Use actionable information to make a decision on remediation. Ensure you don’t miss incidents in the future by automatically adding discovered threat indicators to watch lists.
Key Features
- Automated investigations of incidents
- Artificial intelligence that reasons
- Identification of high priority risks
- Key insights on users and critical assets
IBM QRadar Network Insights
IBM QRadar Network Insights enables attack prediction through real-time network traffic analysis.
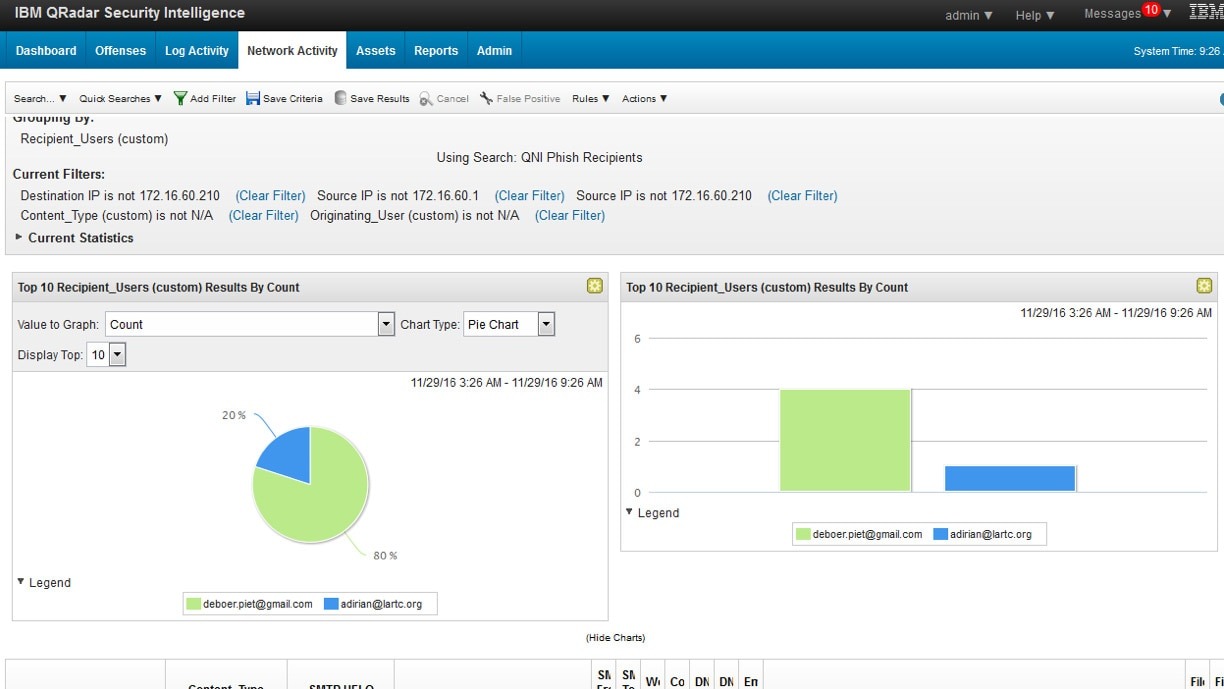
Attackers can’t hide on your network with IBM® QRadar® Network Insights. Security teams are flooded with security log activity every day, but inspecting those logs does not always generate the level of insight required to detect modern threats. They are eager to find additional methods to provide more accurate threat detection. QRadar Network Insights analyzes network data in real-time to uncover an attacker’s footprints and expose hidden security threats in many scenarios before they can damage your organization, including: phishing e-mails, malware, data exfiltration, lateral movement, DNS and other application abuse, and compliance gaps.
Detect Malware Attacks
Discover attacks as they occur with real-time analysis of names, properties, movement and suspect content.
Protect Against Insider Threats
Gain visibility into anomalous lateral network movement and compromised credentials by identifying high-risk users and malicious actions.
Identify Phishing Campaigns
Spot phishing e-mails through increased analysis of sources, targets, subjects and content.
IBM QRadar Incident Forensics
Give enterprise IT security teams better visibility and clarity into security incident-related network activities
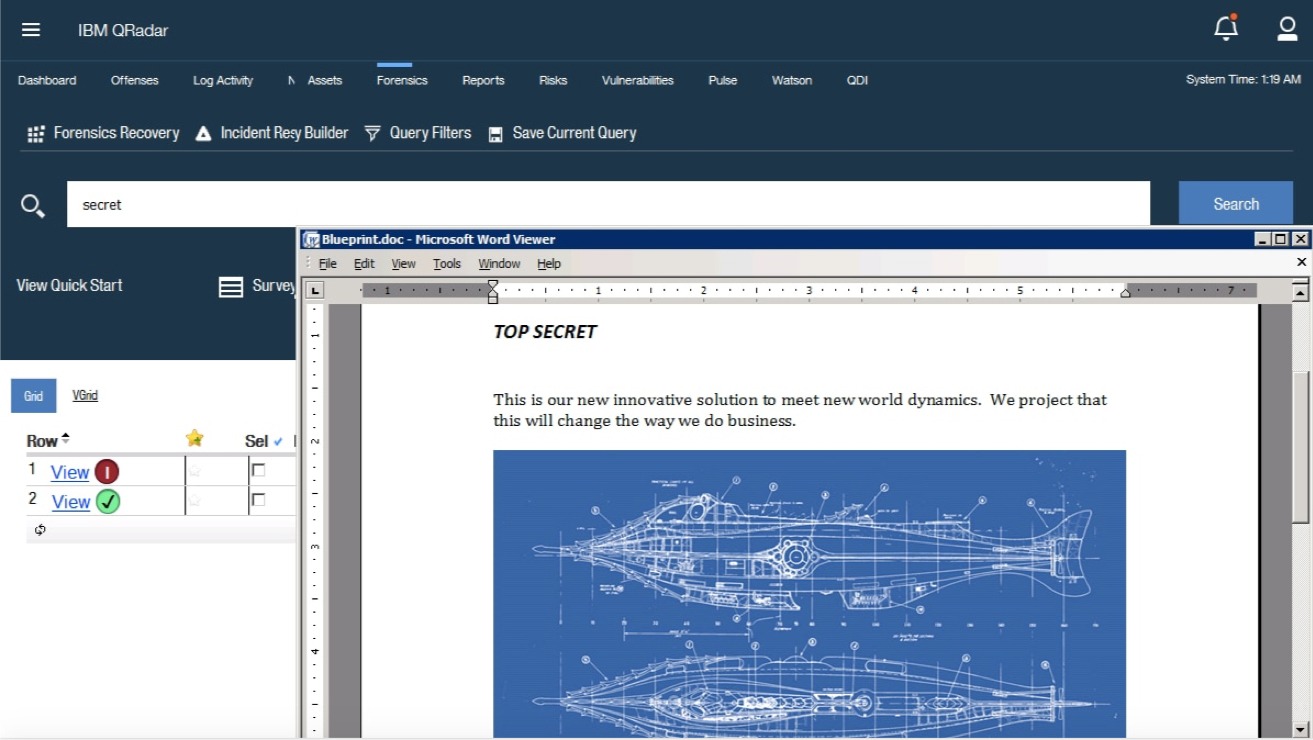
Quickly Conduct Network Forensics Investigations
IBM® QRadar® Incident Forensics allows you to retrace the step-by-step actions of a potential attacker and quickly and easily conduct an in-depth forensics investigation of suspected malicious network security incidents. It reduces the time it takes security teams to investigate QRadar offense records, in many cases from days to hours—or even minutes. It can also help you remediate a network security breach and prevent it from happening again. IBM QRadar Packet Capture appliances are also available to store and manage data if no other network packet capture (PCAP) device is deployed.
Retrace a Cyber Criminal’s Footsteps
Retrace the actions of cyber criminals to provide deep insights into the impact of an intrusion and help prevent reoccurrence.
Reconstruct Data in a Security Attack
Rebuild data involved in a security incident to obtain a detailed, step-by-step view of the offense. Simplify the query process with an interface similar to an internet search engine.
Save Time and Lower Costs
IT security teams can quickly and easily conduct a thorough forensics investigation and gain visibility to the details behind a security breach, with no special skills or training.
Key Features
- Retrace the step-by-step actions of cyber criminals
- Rebuild data and evidence related to a security incident
- Integrates with IBM QRadar Security Intelligence Platform
- Enable threat-prevention collaboration and management
- Integrates with hundreds of IBM and non-IBM products
IBM QRadar Vulnerability Manager
Intelligent vulnerability management that adds context and prioritizes results, enabling you to develop an action plan to address security exposures
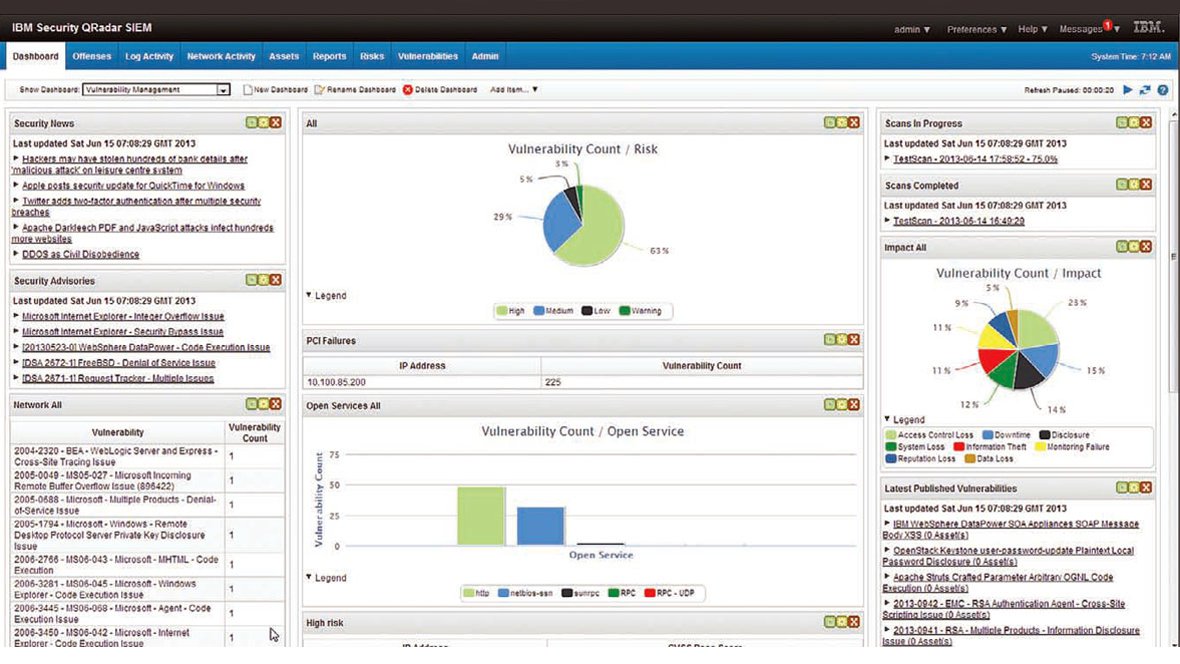
IBM® QRadar® Vulnerability Manager senses security vulnerabilities, adds context and helps prioritize remediation activities. Fully integrated with the QRadar Security Intelligence Platform, it uses advanced analytics to enrich the results of vulnerability scans to lower risk and achieve compliance. QRadar Vulnerability Manager correlates vulnerability data with network topology and connection data to intelligently manage risk. A policy engine automates compliance checks. Using QRadar Vulnerability Manager will help your security team develop an optimized action plan to address security exposures to work more efficiently and decrease costs.
Key Features
- Security breach prevention
- Integration with IBM QRadar Security Intelligence Platform
- Single, consolidated view of vulnerabilities
- Remediation and mitigation activity prioritization
- Regulatory compliance automation
Help Prevent Security Breaches
Senses and highlights over 70,000 known dangerous default settings, misconfigurations and software flaws so you can take corrective action before an attack occurs.
Use Advanced IBM Sense Analytics
Identifies key vulnerabilities and enriches scans with network asset information, security configurations, flow data, logs and threat intelligence to address vulnerabilities and achieve compliance.
Combine and Delineate Data
Saves time and labor by combining data from IBM and third party scanners. Delineates nonthreatening vulnerabilities such as those on inactive applications from critical ones needing attention.
